OIDC Discovery Endpoint - Configuring .well-known in ISAM/ISVA
Contents
Overview
The .well-known endpoint returns OpenID Connect metadata about the authorization server. This information can be used by clients to programmatically configure their interactions with ISAM.
Reverse Proxy Junction Root Method
The reverse proxy junction method involves creating an additional local junction that WebSEAL will use to access files we place on the root path. This method requires IBM Security Verify Access (ISAM/ISVA 10.0.X).
To start off we need to SSH onto the ISAM appliance and create the local junction.
noteCreating the local junction can only be done via the CLI.
ssh -l admin {{ applicance_host }}
isam
admin
pdadmin> login
Enter User ID: sec_master
Enter Password: ********
pdadmin sec_master>
s t {{ object_space }}-webseald-{{ applicance_host }} create -t local /.well-known
acl attach /WebSEAL/{{ object_space }}/.well-known unauthIn the reverse proxy configuration file for the instance we created the local junction for, add the below configuration lines.
This will returnapplication/jsoninstead oftext/htmlas the content-type for any files with the/.well-knownpath.WebSEAL instance configuration file[rsp-header-names:/.well-known]
content-type = application/jsonAdd the OpenId Discovery files to the
junction-rootof the WebSEAL instance. It's important to NOT specify the file type for theopenid-configurationfile as you would otherwise has to enter this for WebSEAL to match on the file.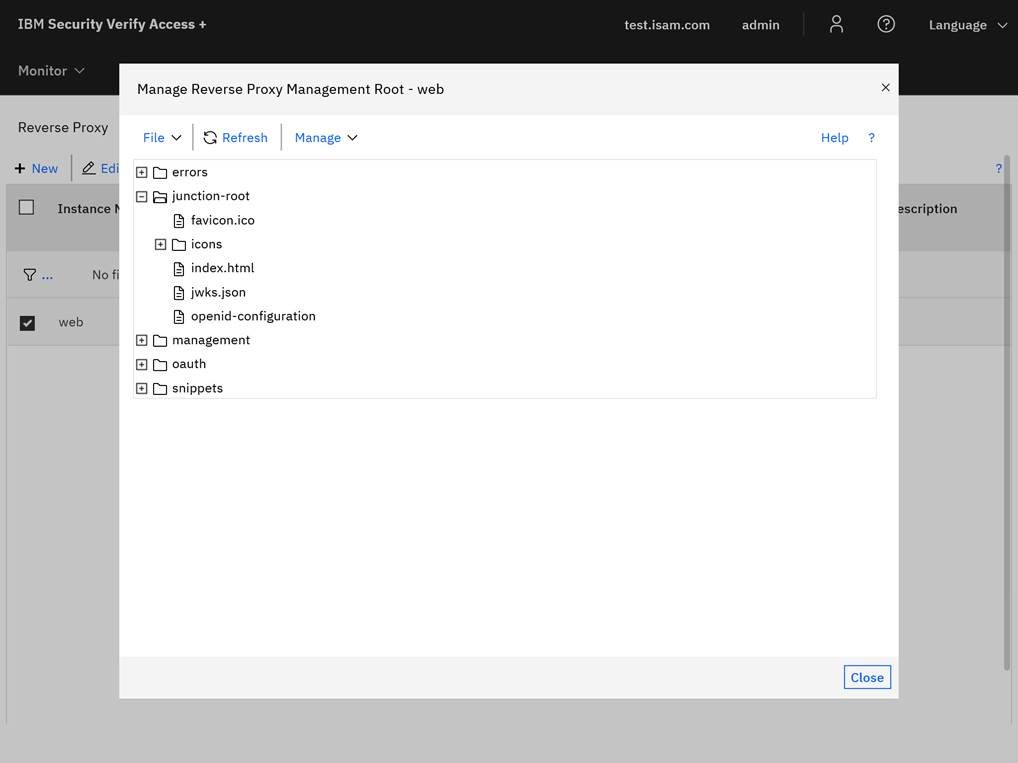
HTTP Transformation Method
/.well-known/openid-configuration Endpoint
To configure the OpenID Connect (OIDC) discovery documents we'll need to add some XSL Transforms (XSLT) and make them accessible on /.well-known/openid-configuration which we'll do with some ACL's.
<?xml version="1.0" encoding="UTF-8" ?>
<xsl:stylesheet xmlns:xsl="http://www.w3.org/1999/XSL/Transform" version="1.0" xmlns:external="http://xsltfunctions.isam.ibm.com">
<xsl:strip-space elements="*" />
<xsl:template match="/">
<HTTPRequestChange>
<xsl:apply-templates />
</HTTPRequestChange>
</xsl:template>
<!-- Define host variable -->
<xsl:variable name="host">
<xsl:value-of select="//HTTPRequest/Headers/Header[@name='host']" />
</xsl:variable>
<xsl:template match="//HTTPRequest/RequestLine/URI">
<xsl:variable name="uri" select="node()" />
<HTTPResponseChange action="replace">
<Version>HTTP/1.1</Version>
<StatusCode>200</StatusCode>
<Header name="Content-Type" action="add">application/json</Header>
<Header name="Access-Control-Allow-Origin" action="add">*</Header>
<Body>{
"issuer":"<xsl:value-of select="$host" />",
"authorization_endpoint":"<xsl:value-of select="$host" />/sso/sps/oauth/oauth20/authorize",
"token_endpoint":"<xsl:value-of select="$host" />/sso/sps/oauth/oauth20/token",
"userinfo_endpoint":"<xsl:value-of select="$host" />/sso/sps/oauth/oauth20/userinfo",
"jwks_uri":"<xsl:value-of select="$host" />/.well-known/jwks.json",
"response_types_supported":["code"],
"grant_types_supported":["authorization_code"],
"subject_types_supported":["pairwise"],
"id_token_signing_alg_values_supported":["RS256"],
"scopes_supported":["openid","profile","email","phone"]
}</Body>
</HTTPResponseChange>
</xsl:template>
</xsl:stylesheet>
/.well-known/jwks.json Endpoint
This one's nice and simple. Just pass the request to a different endpoint and that's it.
<?xml version="1.0" encoding="UTF-8" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:strip-space elements="*" />
<xsl:template match="/">
<HTTPRequestChange>
<xsl:apply-templates />
</HTTPRequestChange>
</xsl:template>
<xsl:template match="//HTTPRequest/RequestLine/URI">
<URI>/sso/sps/oauth/oauth/oauth20/jwks/APP-OIDC-RS256</URI>
</xsl:template>
</xsl:stylesheet>
Attaching the Rules to the Requests - ACL
In IBM Security Access Manager (ISAM), go to Secure Web Settings tab, select Reverse Proxy, select the Instance you want to attach the .well-known configuration to, and in the reverse proxy configuration file, paste the following transformation rule as shown below.
Just remember to have added your XSLT rule to HTTP Transformations and deployed your changes. You will need to have something to attach to your WebSEAL instance.
[http-transformations]
# The following files are currently available for this configuration entry:
oidc-well-known = oidc-well-known.xslt
oidc-well-known-jwks = oidc-well-known-jwks.xslt
[http-transformations:oidc-well-known]
request-match = request:GET /.well-known/openid-configuration*
[http-transformations:oidc-well-known-jwks]
request-match = request:GET /.well-known/jwks*



